Writep autumn crackme from "Kaspersky Lab"
Hello. The name speaks for itself. Event was poorly lit and I only miraculously managed to participate in one. As a result, managed to grab eleventh place and will receive the promised dividends. Let's get to it.
Crake. Or here (greetings from 2к17 if the link is jammed)
/ > Tools: IDA, HxD, CFF Explorer, DbgView, PEChecksum, KmdManager
The last three instruments is quite specific, many crackers have already understood what the whole point of Crake.
After downloading the file it turned out that he has an extension. My head began to climb the dirty thoughts about the fact that this is another ctf stuff a La find how to use me. Hex listing brought me to a state of Ataraxia:
Cherished signatures Mark Zbikowski was in place, we continue the analysis:
Here's the twist — we driver. Safely rename CrackMe in
Looks like the driver is imagebase:
And this is the real DriverEntry:
Here it is necessary to remember the name of the device and to draw attention to the fact that our driver kindly handles usermoney
So the handler looks manual adjustments:
And that's after comparison with the ASM listing:
What's going on here? The function receives the input of a buffer (KST I have not figured out how to transmit means
Experienced cracker patched to this case and have launched a release, Yes, but we need to find the serial number to our mail. Prepare for the worst and go to the sacred functions of the
ASM listing her most intimate moment:
After validation of the obtained parameters, it calculates the hash of a certain string constants, a hash of the input
Looks like the(actually not very). Inside it is another function 4, are doing something with the inbound line: fill, copy, modify, and so on.
It is worth remembering that in the
the
Of course! Heflying Kama bullet is to put a breakpoint after the call to this function, maybe the return line is our keygen (the biggest problem of any CrackMe — trivial strcmp). But there is a couple but:
No matter how I tried, but my thumb on top of VirtualBox with xp sp3 refused to accept Syser/SoftICE/WinDbg. Had an idea: why not force the driver to kindly inform us the serial number? How can I do that?
To start patchin test the validity of the incoming data inside the
Just fill them with NOP AMI.
Then you have to manually fill the buffer with soap (it is dynamically allocated), do it, say, at the beginning of the
Became this:
They were sawed by the dynamic calculation of the length of the email and everything associated with
Now propatchen the end of the function, and instead of performing a
After patching, you must recalculate the CheckSum field of the driver — to do this, use the utility PEChecksum. Then load the driver using KmdManager (to download the x32 driver you are required to have a x32 system, preferably xp), open DebugView. It remains to write a small program to call the driver:
the
Compile, run:
The first line is the required serial number. This is good-bye.
Article based on information from habrahabr.ru
Crake. Or here (greetings from 2к17 if the link is jammed)
/ > Tools: IDA, HxD, CFF Explorer, DbgView, PEChecksum, KmdManager
The last three instruments is quite specific, many crackers have already understood what the whole point of Crake.
After downloading the file it turned out that he has an extension. My head began to climb the dirty thoughts about the fact that this is another ctf stuff a La find how to use me. Hex listing brought me to a state of Ataraxia:
tucked under a spoiler

Cherished signatures Mark Zbikowski was in place, we continue the analysis:
tucked under a spoiler

Here's the twist — we driver. Safely rename CrackMe in
crackme.sys. This time came up with the pertinent question: where is the loader? Where is the GUI(graphical user interface, do not think anything bad)? They are not. Literally. I think it's the second (hehe, to get first yet) is illogical, CrackMe: it does not happen. We continue the analysis.Looks like the driver is imagebase:
tucked under a spoiler

And this is the real DriverEntry:
tucked under a spoiler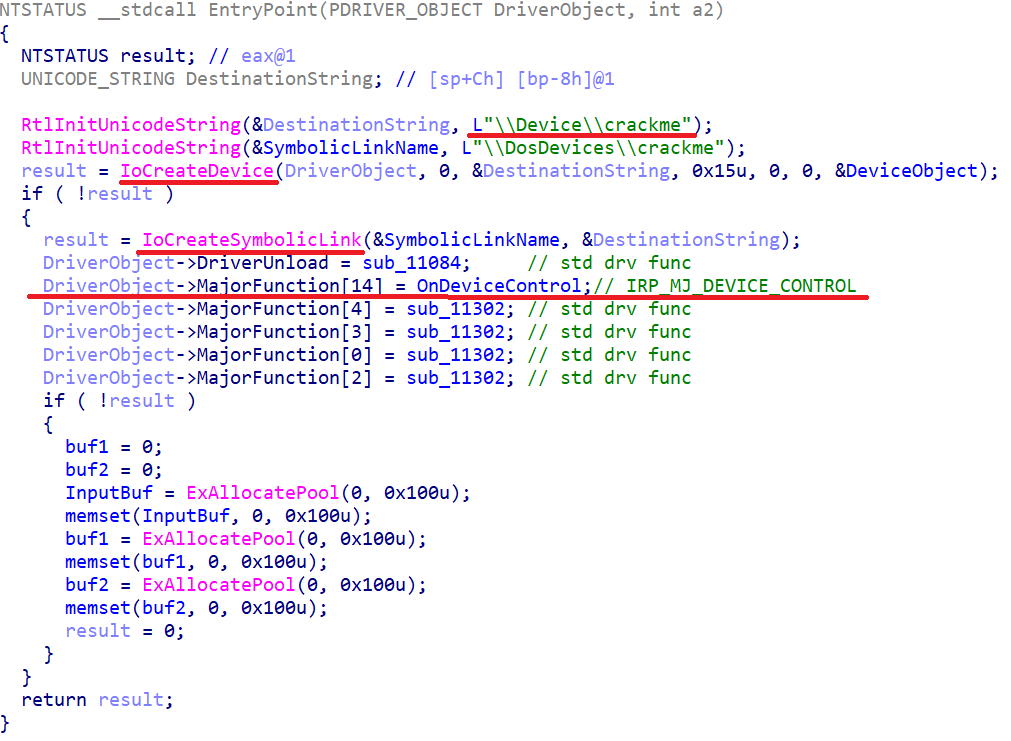

Here it is necessary to remember the name of the device and to draw attention to the fact that our driver kindly handles usermoney
DeviceIoControl. So the handler looks manual adjustments:
tucked under a spoiler

And that's after comparison with the ASM listing:
tucked under a spoiler

What's going on here? The function receives the input of a buffer (KST I have not figured out how to transmit means
DeviceIoControl, write in the comments), and a control code. Buffer depending on ControlCode is copied to the mail or keygen (class emulation GUI, che said). After you complete these fields for the third time we need to send ControlCode and this will start a Validate, which displays a message.Experienced cracker patched to this case and have launched a release, Yes, but we need to find the serial number to our mail. Prepare for the worst and go to the sacred functions of the
Validate:tucked under a spoiler

ASM listing her most intimate moment:
tucked under a spoiler

After validation of the obtained parameters, it calculates the hash of a certain string constants, a hash of the input
buf1 (our mail, obviously) and a General hash of these two lines.Looks like the
func1? Scary and awful It is worth remembering that in the
func1 we do not share anything that would be associated with the buf2 (this is obviously our serial). And what does cracker when he sees a certain hash function from mail which is not transmitted anything associated with the keygen, and right after that lovely combination of:the
xor eax, eax
repe cmpsb
setz al
ret
Of course! He
-
the
- We need to properly initialize the function call
Validatethrough a series of requests to the driver (or handles call + to patch memory)
the - Common debugger archetype of the "Olga" for ring0 is not suitable — you need to use the tools more powerful
No matter how I tried, but my thumb on top of VirtualBox with xp sp3 refused to accept Syser/SoftICE/WinDbg. Had an idea: why not force the driver to kindly inform us the serial number? How can I do that?
To start patchin test the validity of the incoming data inside the
Validate:tucked under a spoiler

Just fill them with NOP AMI.
Then you have to manually fill the buffer with soap (it is dynamically allocated), do it, say, at the beginning of the
Validate. It was this:tucked under a spoiler

Became this:
tucked under a spoiler

They were sawed by the dynamic calculation of the length of the email and everything associated with
buf2. Now propatchen the end of the function, and instead of performing a
repe cmpsb will try to force the call to DbgPrint:tucked under a spoiler

After patching, you must recalculate the CheckSum field of the driver — to do this, use the utility PEChecksum. Then load the driver using KmdManager (to download the x32 driver you are required to have a x32 system, preferably xp), open DebugView. It remains to write a small program to call the driver:
the
char tmp[0x100];
HANDLE handle = CreateFile(L"\\\\.\\crackme", GENERIC_READ | GENERIC_WRITE, FILE_SHARE_READ | FILE_SHARE_WRITE, 0, OPEN_EXISTING, FILE_ATTRIBUTE_NORMAL, 0);
DeviceIoControl(handle, 0x222408, 0, 0, &tmp, 0x100, &tmp, 0);
CloseHandle(handle);
Compile, run:
tucked under a spoiler

The first line is the required serial number. This is good-bye.
NOTE: the Decision was published right after the job is done the first fifteen participants. You need to respect fair competition.
Comments
Post a Comment